I rarely check my Junk folder, so I’m not up to date with the latest scam attempts. However, I did check it today and noticed a subject that caught my attention: “I RECORDED YOU”. I immediately realized it’s a crypto scam attempt, though I wanted to share it just to make anyone aware that this is truly a scam and to remove it as soon as possible:
Hello there!Unfortunately, there are some bad news for you.Some time ago your device was infected with my private trojan, R.A.T (Remote Administration Tool), if you want to find out more about it simply use Google.My trojan allowed me to access your files, accounts and your camera.Check the sender of this email, I have sent it from your email account.To make sure you read this email, you will receive it multiple times.You truly enjoy checking out porn websites and watching dirty videos, while having a lot of kinky fun.I RECORDED YOU (through your camera) SATISFYING YOURSELF!After that I removed my malware to not leave any traces.If you still doubt my serious intentions, it only takes couple mouse clicks to share the video of you with your friends, relatives, all email contacts, on social networks, the darknet and to publish all your files.All you need is $1500 USD in Bitcoin (BTC) transfer to my account.After the transaction is successful, I will proceed to delete everything.Be sure, I keep my promises.You can easily buy Bitcoin (BTC) here:https://cex.io/buy-bitcoinshttps://nexo.com/buy-crypto/bitcoin-btchttps://bitpay.com/buy-bitcoin/?crypto=BTChttps://paybis.com/https://invity.io/buy-cryptoOr simply google other exchanger.After that send the Bitcoin (BTC) directly to my wallet, or install the free software: Atomicwallet, or: Exodus wallet, then receive and send to mine.My Bitcoin (BTC) address is: 1EfCwNrGgGbNAn4bKUX7XydSzFu4RHheC4Yes, that’s how the address looks like, copy and paste my address, it’s (cAsE-sEnSEtiVE).You are given not more than 3 days after you have opened this email.As I got access to this email account, I will know if this email has already been read.Everything will be carried out based on fairness.An advice from me, regularly change all your passwords to your accounts and update your device with newest security patches.
The FROM email address was actually showing my own email address, but luckily the SPF check failed which means my email wasn’t compromised, instead they are using a spoofing attempt. Office caught it in the junk folder:
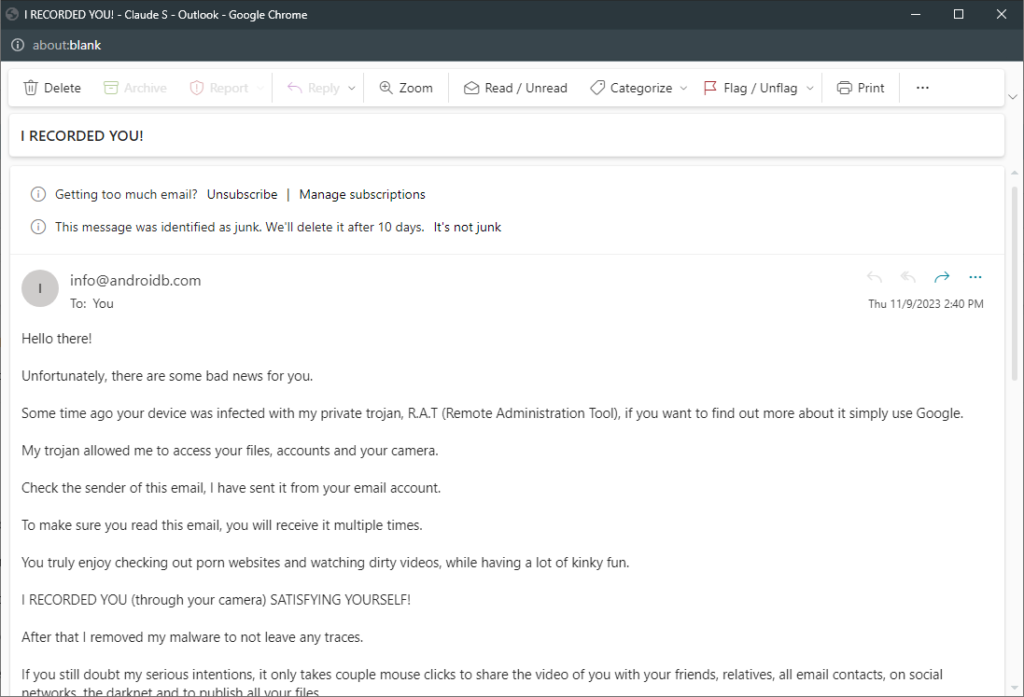
In fact, here is the partial header of the messages:
Received: from DB9P195MB2159.EURP195.PROD.OUTLOOK.COM (2603:10a6:10:3d7::5) by GV1P195MB1812.EURP195.PROD.OUTLOOK.COM with HTTPS; Thu, 9 Nov 2023 12:40:04 +0000
Received: from MW4PR04CA0306.namprd04.prod.outlook.com (2603:10b6:303:82::11) by DB9P195MB2159.EURP195.PROD.OUTLOOK.COM (2603:10a6:10:3d7::5) with
Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.6977.18; Thu, 9 Nov 2023 12:40:02 +0000
Received: from MW2NAM10FT101.eop-nam10.prod.protection.outlook.com (2603:10b6:303:82:cafe::7e) by MW4PR04CA0306.outlook.office365.com (2603:10b6:303:82::11) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.6977.18 via Frontend Transport; Thu, 9 Nov 2023 12:40:01 +0000
Authentication-Results: spf=softfail (sender IP is 169.239.120.241)
smtp.mailfrom=androidb.com; dkim=none (message not signed)
header.d=none;dmarc=none action=none header.from=androidb.com;
Received-SPF: SoftFail (protection.outlook.com: domain of transitioning
androidb.com discourages use of 169.239.120.241 as permitted sender)
Received: from [169.239.120.241] (169.239.120.241) by MW2NAM10FT101.mail.protection.outlook.com (10.13.154.63) with Microsoft SMTP
Server id 15.20.6977.18 via Frontend Transport; Thu, 9 Nov 2023 12:39:57 +0000
X-IncomingTopHeaderMarker: OriginalChecksum:ED77AA4AC43450294AEA9B80E1BC82F71A288C985B718B5910D1A4119CB420EB;UpperCasedChecksum:1A808335B6CE8F1E42AC0BA3F4CD6D1B13BE53980502FA16566824AF8F136476;SizeAsReceived:379;Count:9
Received: from kptacen ([90.103.117.36]) by 75739.com with MailEnable ESMTP; Thu, 9 Nov 2023 13:40:01 +0100
I highlighted the “fun” parts:
- the originating IP belongs to ILNET TELECOM GROUP SARL, a net provider in N’Djaména, Chad, so Africa
- however, there’s another header from the original sender, that shows 75739.com as the sending domain. This is a parked domain for sale, which is in Chinese. Its sending IP is a French one, 90.103.117.36 so this spammer is using some compromised computers to send this crypto scam.
- in its original scam email, the scammer mentions this BTC address: 1EfCwNrGgGbNAn4bKUX7XydSzFu4RHheC4 – I verified it and luckily there’s no incoming crypto, which means they didn’t fool anyone yet.